
CyberSec Roundup
A synopsis of the latest Cybersecurity News
SolarWinds Attack
The major activity last week was around the SolarWinds attack as a number of businesses and government entities were affected. Last week we covered the sophisticated FireEye hack, but now we know more details and how this is connected to the SolarWinds attack.
The Company
The Solarwinds company develops network monitoring software which is used by companies worldwide, including many Fortune 500 businesses and US government departments. The SolarWinds Orion platform was hacked earlier in the year, and the breach went undetected. As the FireEye hack was being investigated, they realized that the breach came via the SolarWinds Orion platform, and thus the SolarWinds hack was discovered.
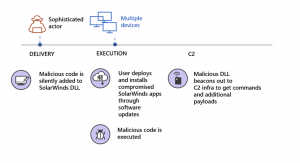
The Attack
The hackers managed to access SolarWinds Orion’s build system, where they inserted malicious code into a legitimate DLL file. Orion’s update system would then be used to distribute this infected file to customers who are using the platform. This file would be loaded and the malicious code would be executed to create the backdoor for the attacker to gain access. Once the attacker is in, it is just a matter of time before they gain high level credentials and fully exploit the network.
Attack Scope
The attack has had a major impact, as it is believed that approximately 18,000 of SolarWinds’ customers were hit. Many organizations are still trying to determine if they were compromised, but beyond FireEye, we know that many US government departments such as Homeland Security and National Institute of Health were hit. Cisco and Microsoft have also confirmed they were affected.
The Attackers
When FireEye was hacked it was believed to be state sponsored and that hasn’t changed. The Russian APT group Cozy is believed to be the culprit, but other Russian groups APT groups (UNC2452 and Dark Halo) are also being looked at.
By: David Pinder
IT & Security Consultant
Certified Ethical Hacker




